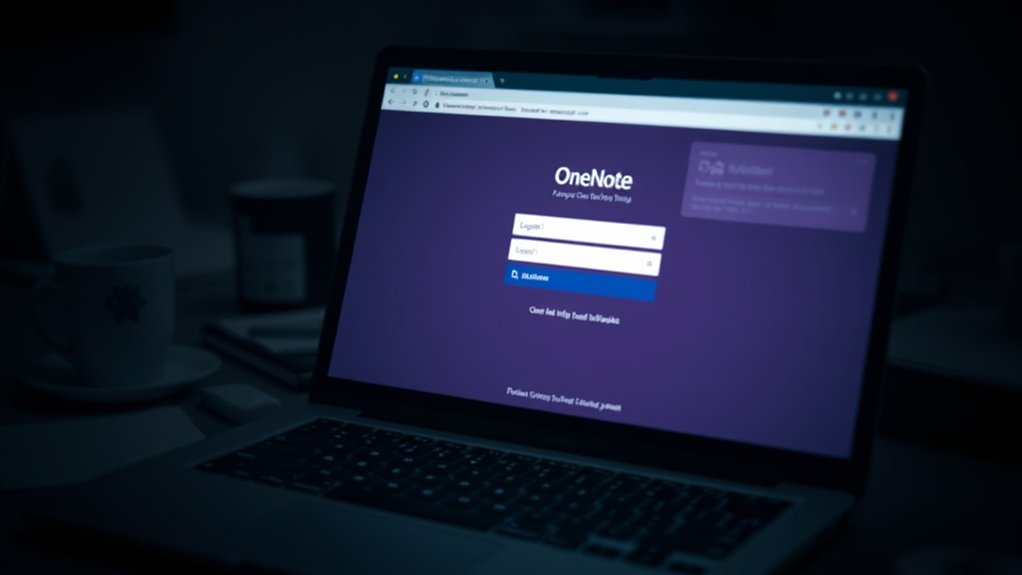
In a troubling development for internet security, a phishing campaign disguised as a OneNote login interface has been targeting users in Italy and the United States since January 2022. This sophisticated attack method utilizes fake OneNote login pages to steal Office365 and Outlook credentials from unsuspecting victims. The exploit has garnered attention owing to its effective use of legitimate hosting platforms, including Notion, Google Docs, and Glitch, which researchers suggest complicates detection efforts. Additionally, these attacks often involve the utilization of free cloud platforms to further enhance their credibility.
A phishing campaign masquerading as a OneNote login interface threatens users in Italy and the U.S., exploiting legitimate platforms for credential theft.
Victims often receive emails with enticing subject lines such as “New Document Shared with you,” prompting them to click on links that lead to the fraudulent pages. Once there, users are presented with familiar authentication options, including entries for Office365 and Outlook accounts. Attackers increasingly exploit legitimate file hosting services to bolster the credibility of their phishing attempts. Experts recommend enabling two-factor authentication as a crucial defense against unauthorized access attempts.
In a concerning technical twist, the phishing pages employ advanced JavaScript to not just capture the victims’ credentials but additionally their IP addresses, using the ipify.org service for this purpose.
Data exfiltration occurs via Telegram bots, which use hardcoded tokens and chat IDs to transmit the stolen information to remote servers. Following this, victims are deceptively redirected to the legitimate Microsoft login page, further obfuscating the attack. This tactic markedly reduces the likelihood of immediate detection, as investigators often focus on suspect links rather than legitimate-looking interfaces.
Given the ongoing nature of this campaign, which has lasted for over three years, experts highlight the importance of public awareness and cybersecurity hygiene. Advisories suggest users should manually type URLs or utilize established bookmarks rather than clicking on potentially malicious links.
They likewise recommend reporting phishing attempts directly through services like Outlook and being cautious of any platforms that capture IP addresses. As the phishing campaign matures, its techniques continue to evolve, demanding vigilance from users and security professionals alike. The increasingly sophisticated methods employed by attackers pose serious challenges for internet security frameworks and the protection of sensitive online data.